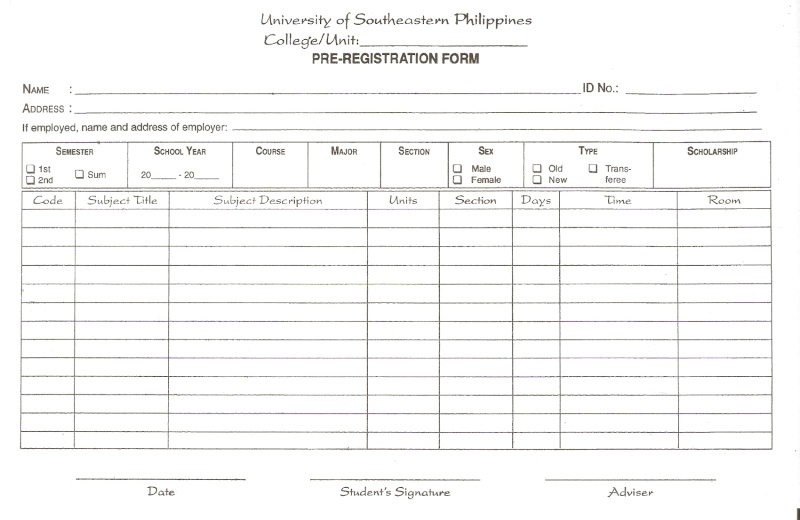
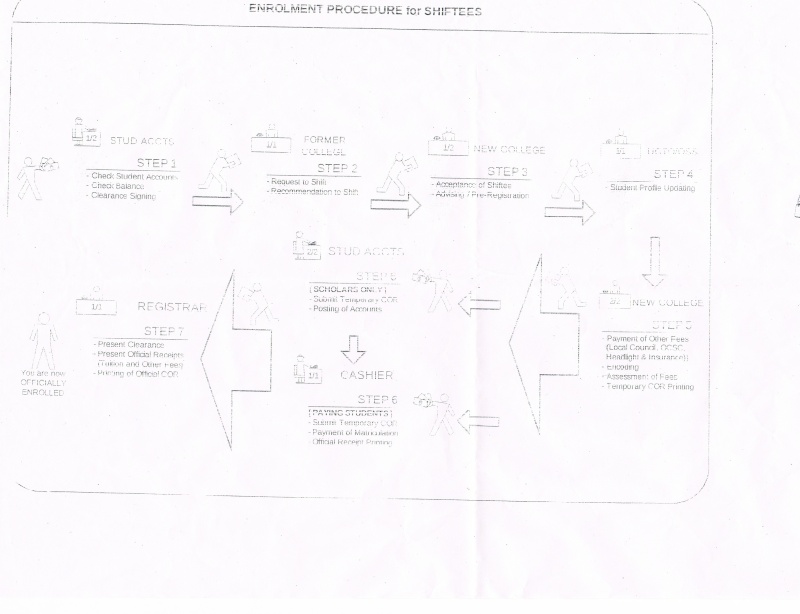
Interview your university network specialist. Ask how various parts of the system communicate with each other throughout the university. (Q) Given the chance to redesign the existing setup, enumerate and discuss your key points for an effective and efficient network environment ideal for the university.
(at least 3000 words)
Basically, all of our answers are all the same because we submitted a questionnaire to Sir Ariel Reyes as a class. We set a schedule for the interview with Sir Ariel Reyes last week but unfortunately there are problems occurred when the planned interview was about to take progress; the server had a problem so Sir Ariel Reyes needs to cut the planned session and move it to another time, but due to Sir Ariel’s busy schedule we didn’t had a chance to have a class discussion. So, the planned class discussion failed because due to some conflicts, later it turned out to be just leaving Sir Ariel Reyes a questionnaire so that he could answer all of the questions. Unfortunately, he didn’t answer all of the questions, so my answers are all base on Sir Ariel’s answers.
These were the questions that the class had come up with.
Questions:
1. In system development, how various parts of the system communicate with each other throughout the university? In what way?
2. What are the components involved in the system(s) in the university? (hardware, software, technology, etc.)
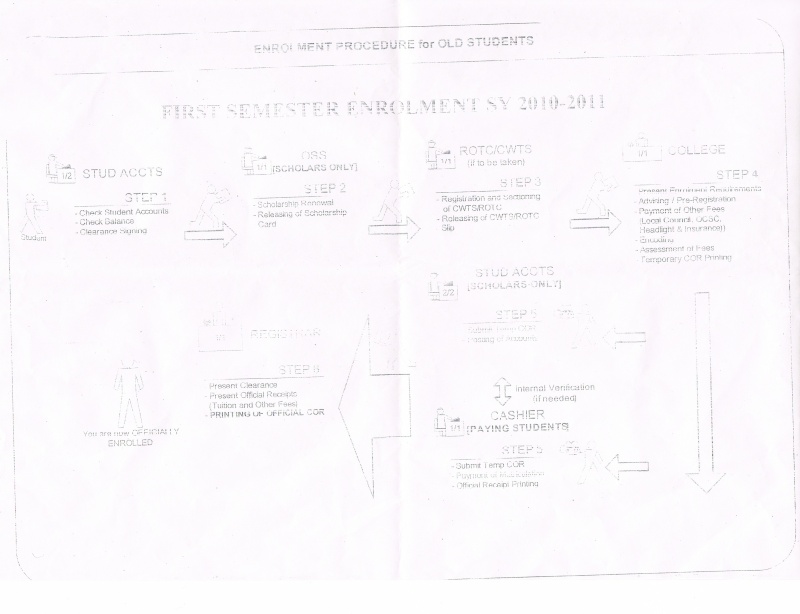
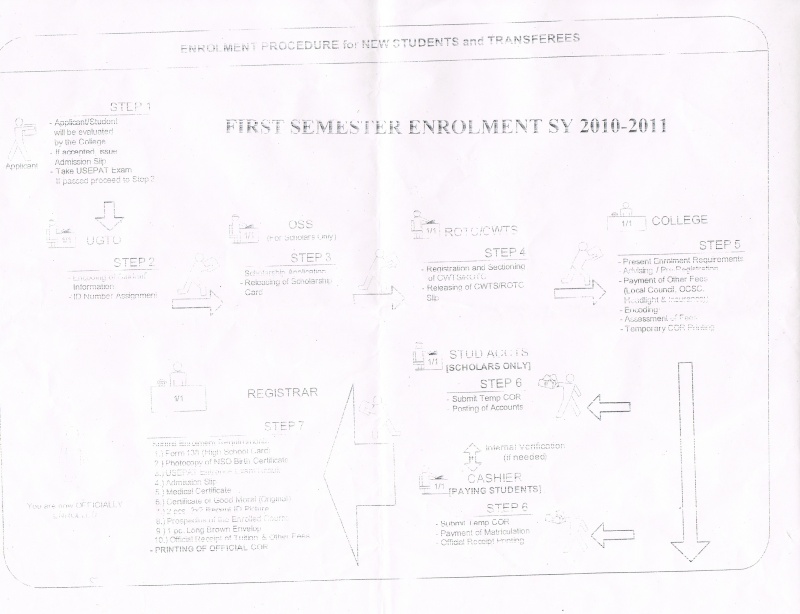
3. How do these communicate with one another? (topology, network connectivity, protocols, etc.) – may include data flow/ UML diagrams to better explain
4. What are the processes involved in the communication (each system to other systems)?
5. How do you go along with the maintenance of the system?
6. Does the system follow a specific standard? Explain Please.
7. How is the security of the system? Are there any vulnerabilities? Risks? Corresponding mitigation techniques? Access control?
8. Are there any interference? During what (most) times do these occur? Explain their effects especially with regards to the business of the university?
9. What are the current trends in network environment ideal for the university?
10. Based on your experience, can you enumerate and discuss your key points for an effective and efficient network environment that is ideal for the university?
11. Can those key points apply to the current trends for the university’s network environment? How it works?
12. Can you draw the general network architecture of the university?
13. On your own opinion, are the users satisfied with the current network setup?
14. What network architecture is used in the university?
15. What are the drawbacks that you found in the existing system? How would you treat these drawbacks?
16. On you own opinion; are there any changes that you want to change in the existing network architecture?
17. How would you see the university few years after implementing the newly developed system?
So basically, those where the questions that we had come up with and below are the answers that Sir Ariel Reyes had come up with.
• In system development, how various parts of the system communicate with each other throughout the university? In what way?
Answer of Sir Reyes:
Regarding System Development, the best person to ask is our University Programmers, Mr. Fortich and Dr. Mercado.
So here, Sir Ariel Reyes recommended Sir Japh Fortich and Maam Tammy Mercado to answer about the first question. I tried to communicate with Sir Japh but unfortunately I didn’t get him due to busy schedules.
• What are the components involved in the system(s) in the university? (hardware, software, technology, etc.)
Answer of Sir Reyes:
I am not in the right position to discuss the details of the software components used as there are other assigned personnel for such job. However, talking about hardware component and technology used, basically I, assigned as the network administrator, is entrusted to maintain our different servers to run 24/7. Currently, we have our Web Server hosted here in our University in our HP ProLiant ML350 Server. Its an old but stable server set-up here in our Networks Office and has been active since Engr. Val A. Quimno , not yet a dean, was appointed as the Network Administrator. The said server has the following specification:
-Intel Xeon 3.0 GHz, 3.2 GHz, or 3.4 GHz processors (dual processor capability) with 1MB level 2 cache standard. Processors include support for Hyper-Threading and Extended Memory 64 Technology (EM64T)
-Intel® E7520 chipset
-800-MHz Front Side Bus
-Integrated Dual Channel Ultra320 SCSI Adapter
-Smart Array 641 Controller (standard in Array Models only)
-NC7761 PCI Gigabit NIC (embedded)
-Up to 1 GB of PC2700 DDR SDRAM with Advanced ECC capabilities (Expandable to 8 GB)
-Six expansion slots: one 64-bit/133-MHz PCI-X, two 64-bit/100-MHz PCI-X, one 64-bit/66-MHz PCI-X, one x4 PCI-Express, and one x8 PCI-Express
-New HP Power Regulator for ProLiant delivering server level, policy based power management with industry leading energy efficiency and savings on system power and cooling costs
-Three USB ports: 1 front, 1 internal, 1 rear
-Support for Ultra320 SCSI hard drives (six hot plug or four non-hot plug drives supported standard, model dependent)
-Internal storage capacity of up to 1.8TB; 2.4TB with optional 2-bay hot plug SCSI drive
-725W Hot-Plug Power Supply (standard, most models); optional 725W Hot-Pluggable Redundant Power Supply (1+1) available. Non hot plug SCSI models include a 460W non-hot plug power supply.
-Tool-free chassis entry and component access
-Support for ROM based setup utility (RBSU) and redundant ROM
-Systems Insight Manager, SmartStart, and Automatic Server Recovery 2 (ASR-2) included
-Protected by HP Services and a worldwide network of resellers and service providers. Three-year Next Business Day, on-site limited global warranty. Certain restrictions and exclusions apply. Pre-Failure Notification on processors, memory, and SCSI hard drives.
Aside from it, our mail server running under Compaq Proliant ML330 Server, our oldest server, is also hosted here in our Networks Office. Together with other Servers, such as Proxy and Enrollment Servers, both proxy and our enrollment servers are running in a microcomputer/personal computer but with higher specifications to act as servers.
• How do these communicate with one another? (topology, network connectivity, protocols, etc.) – may include data flow/ UML diagrams to better explain.
Answer of Sir Reyes:
All Servers are connected in a shared medium grouped as one subnetwork. In general, our network follows the extended star topology which is connected to a DUAL WAN Router that serves as the load balancer between our two Internet Service Providers. All other workstations are grouped into different subnetworks as in star topology branching out from our servers subnetwork as in extended star topology. At present, we are making use of class C IP Address for private IP address assignments. Other workstations IP assignments are configured statically (example: laboratories) while others are Dynamic (example: offices). All workstations are connected via our proxy servers that do some basic filtering/firewall to control users access to the internet aside from router filtering/firewall management. So, whenever any workstation has to connect to the internet, it has to pass through software and hardware based firewall.
• What are the processes involved in the communication (each system to other systems)?
Answer of Sir Reyes:
As mentioned above, in item 3, all workstations are connected via a proxy server. It means that whenever a workstation is turned on, it requests for an IP address from the proxy server (for dynamically configured IP address) and connect to the network after IP address is acquired. As connection is established, each system can now communicate and share resources within the same subnetwork and to server following the concepts discuss in your Computer Network Class.
• How do you go along with the maintenance of the system?
Answer of Sir Reyes:
Basically, our servers are expected to be in good condition since it is required to be up 24/7. Daily, during my vacant period, monitoring on the servers are observed that includes checking logs, checking hardware performance such as CPU health, etc. If problems are observed, remedies are then and then applied. Once in a week, regular overall checkup is observed as preventive maintenance to ensure not to experience longer downtime if possible.
• Does the system follow a specific standard? Explain Please.
Answer of Sir Reyes:
As I was appointed as the Network Administrator, everything was already in place except for some minor changes. Basically, different networking standards was already observed such as cabling standards, TIA/EIA 568A-B, different IEEE standards as discussed in your Computer Networks Subject, etc.
• How is the security of the system? Are there any vulnerabilities? Risks? Corresponding mitigation techniques? Access control?
Answer of Sir Reyes:
As I have mentioned, we have implemented both software and hardware based filtering/firewall. Basically, Risks or vulnerabilities and different mitigation techniques were considered to increase security in our network. Aside from filtering/firewall, constant monitoring on networks activity also increases the security of the system.
• Are there any interference? During what (most) times do these occur? Explain their effects especially with regards to the business of the university?
Answer of Sir Reyes:
Major Interferences are normally encountered as an effect of unforeseen and beyond our control events such as black outs, and the like. The said interference would of course affect University’s day-to-day businesses for obviously this will paralyze all our activities that rely on electricity and further this might cause damage on our network devices, etc. that may later be the reason for longer downtime. Problems encountered by our providers such as connection to the National/International Gateway also affect University’s business such as correlating to University’s Business Partners outside and within the country.
• What are the current trends in network environment ideal for the university?
• Based on your experience, can you enumerate and discuss your key points for an effective and efficient network environment that is ideal for the university?
• Can those key points apply to the current trends for the university’s network environment? How it works?
• Can you draw the general network architecture of the university?
• On your own opinion, are the users satisfied with the current network setup?
• What network architecture is used in the university?
• What are the drawbacks that you found in the existing system? How would you treat these drawbacks?
• On you own opinion; are there any changes that you want to change in the existing network architecture?
• How would you see the university few years after implementing the newly developed system?
As you can see, Sir Ariel Reyes hasn’t answered all of the questions because he explained that no time and he has a very tight schedule. Luckily, for us he manages to answer at least some of the questions.
In relevant to the second question about given the chance to redesign the existing setup, enumerate and discuss your key points for an effective and efficient network environment ideal for the university.
For me it all begins with a plan. Plan what is the best way to improve the network environment of the university. Planning on the thing that needs to be improved, these are the requirements of the university. What are the important processes that the university really relies on, from the businesses to school related processes such as enrollment and other processes. As we all know the university has some business related establishment that currently servicing customers such as the university dormitory. In relation to network communication, do the university dormitory needs to have a better network environment for communication or are they satisfied with it? so by looking at that we can get the requirements that is needed for the improvement. Now, we go to the enrollment system of the university, does the processes satisfying? or not? So it is really base on the requirement. After the requirements are set, the next thing to do is to analyze if what are the best solutions for the requirements. Do we need to relocate the servers? Do we need to change the server? Or do we need to change the specs of the server? These are the thing that needs to be considered. So after analysis, the next thing to do is design. What are the things to do when designing? What topology are we going to use in order to attain the said requirements. What standard are we going to use in designing the network environment? So these are the questions that would basically pop out when you want to design a network environment. As the design goes on, the next thing to do is to get started.
Here are some factors that affect network performance. Unfortunately, not all networks are the same. As data is broken into component parts (often known frames, packets, or segments) for transmission, several factors can affect their delivery.
• Latency: It can take a long time for a packet to be delivered across intervening networks. In reliable protocols where a receiver acknowledges delivery of each chunk of data, it is possible to measure this as round-trip time.
• Packet loss: In some cases, intermediate devices in a network will lose packets. This may be due to errors, to overloading of the intermediate network, or to intentional discarding of traffic in order to enforce a particular service level.
• Retransmission: When packets are lost in a reliable network, they are retransmitted. This incurs two delays: First, the delay from re-sending the data; and second, the delay resulting from waiting until the data is received in the correct order before forwarding it up the protocol stack.
• Throughput: The amount of traffic a network can carry is measured as throughput, usually in terms such as kilobits per second. Throughput is analogous to the number of lanes on a highway, whereas latency is analogous to its speed limit.
These factors, and others (such as the performance of the network signaling on the end nodes, compression, encryption, concurrency, and so on) all affect the effective performance of a network. In some cases, the network may not work at all; in others, it may be slow or unusable. And because applications run over these networks, application performance suffers. Various intelligent solutions are available to ensure that traffic over the network is effectively managed to optimize performance for all users.
And also, network configuration management refers to setting, changing, collecting and restoring information about network devices (bridges, routers, workstations, servers, switches and others).
Networks of any size are in a constant state of flux. Any of the engineers responsible for the network can change the configuration of the switches and routers at any time. Configuration changes to live equipment can have devastating effects on the reliability of the network and the services provided by it. The aim of network configuration management is to save you time & reduce errors on your network due to misconfiguration of network devices. A network configuration management system is designed to allow you to take control of network changes, to simplify the job of managing networks and to fix configuration errors quickly.
There are direct correlations between properly configured devices and network security. Today's network configuration management solutions are specifically designed to automate the process of changing, securing and managing devices throughout the network. Whether configuration changes are introduced through malicious attacks, manual update errors, or network product defects, devices can become vulnerable and place the business at risk.
So, for me I would suggest that we would really have our own building that is properly located in a good space. Then, we will put up the server in that building. So that it would be spacious and the network administrators can easily move in the server room with good space for be able to make good use of the time specially when you have server crashes and server down. The more space you have the better your work is because you can free work on problems when occurred. Next would be good network architecture. The more the architecture is the better the service it can offer. Example, cables that are properly arranged makes a better connection. No entangling of wires and cables. And it can also be a very good atmosphere when you are inside the server room. Next, is good ventilation and good cooling system for all of the hardware that is currently running, the more it gives good performance. As it is all set, the next thing to do is have a more adequate server unit. I’m not against of the specs of our server but it’s kind of old and needs a better one. But, if it is still at good condition and meets the requirements needed for the university then I shall say go. But, as we all know all things has its limits, maybe we need to let it go. The next point I want to say is that the network topology. With good network topology I think all communications throughout the university will be with no problem. There will be some problems but it is minimal, and with a proper security features I think its all going to be ok. As it is all set, the next thing to do is the maintenance. Once it is operational the main thing that should be done is the maintenance. So, it should have a weekly maintenance.
One thing that I want to point out is that our network security. As Sir Val Quimno told us, the security level of our network is not very high. It is prone to all attacks and unwanted events. So for me, they really need to focus on the security so that attacks cannot penetrate the system. And it can lessen the problems in a network environment. So if this are all been done and meet I guess it’s a good network environment.
References:
http://en.wikipedia.org/wiki/Network_performance_managementhttp://www.networkdictionary.com/networking/ncm.php